Secrets
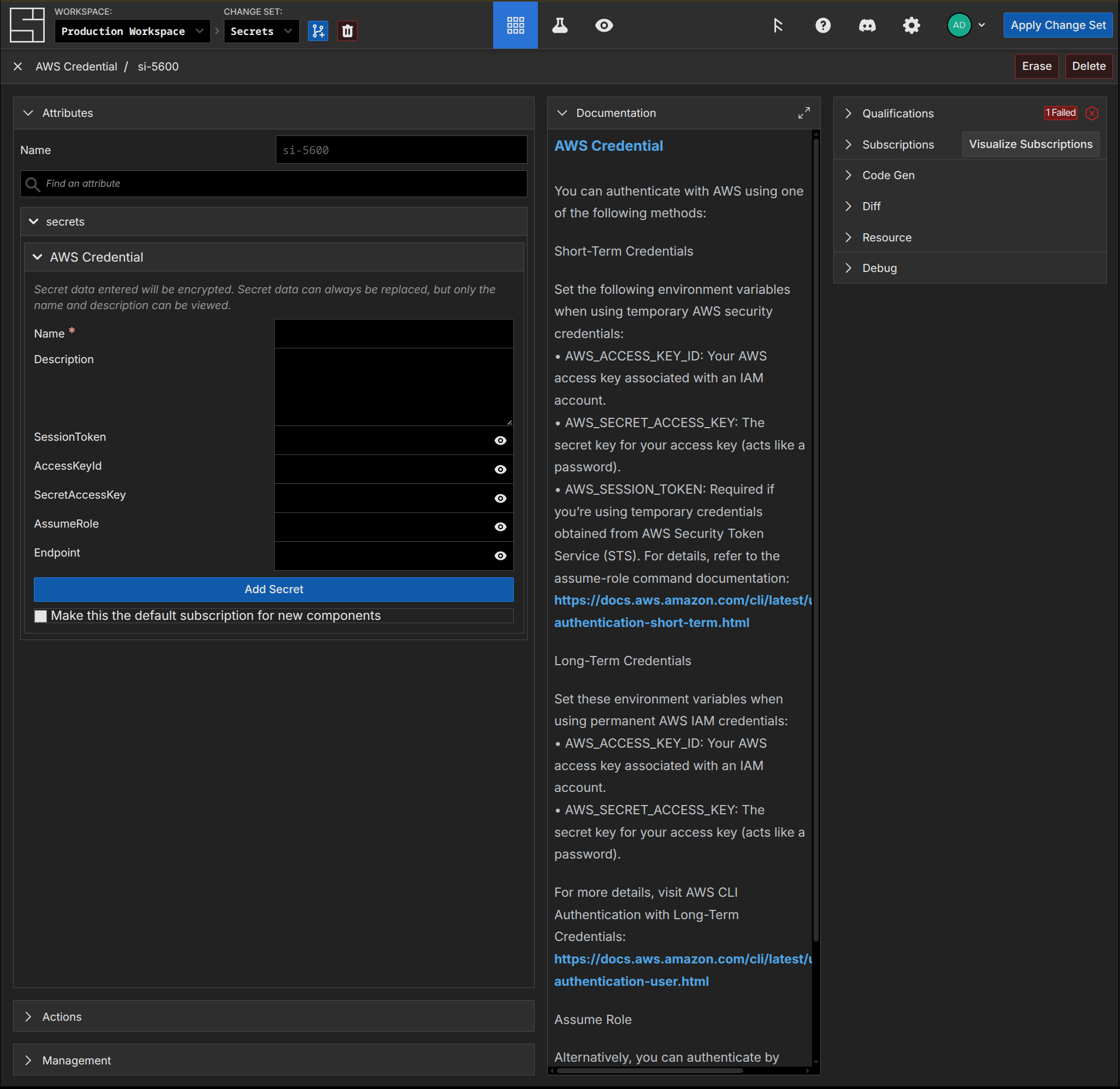
Secrets in System Initiative represent any confidential data, such as login information, API tokens, passwords, etc.
They are end-to-end encrypted, both within the application, on the wire, and at rest.
Encryption Strategy
System Initiative is a multi-tenant system that starts with an 'installation' of System Initiative. For most people, this means our SaaS platform - but it can also mean a local development instance, a Bring Your Own Cloud (BYOC) instance, or a custom installation. Each installation of System Initiative generates an Ed25519 Public Key Pair for the installation. This is the cluster key.
Each workspace generates an Ed25519 Public Key Pair specific to it. The private side of the key is encrypted with the cluster key, which ensures that it is encrypted at rest (even if the database is compromised and dumped in plain text). It cannot be retrieved without the corresponding cluster key. This is the workspace key.
When a secret is put into System Initiative, it is first encrypted with the public workspace key for the workspace it is destined for. This ensures that your secret is also encrypted at rest and cannot be retrieved without the corresponding cluster key and workspace key.
When one of your secrets is needed, we decrypt it and inject it into the micro-vm assigned to your function.
Redaction
Should the secret appear in any logs or output, it will be automatically redacted. System Initiative will not leak your secrets.
WARNING
No programmable system is perfectly secure against secret exfiltration. You must still trust the underlying function code that your secret is being used by.
All "built-in" schemas provided by System Initiative have been vetted for exfiltration risk.
Creating a Secret
$ si secret create "AWS Credential" --name "aws-credential-dev" --use-local-profile
✨ info si Creating change set: Create AWS Credential - 1765498265932
✨ info si Discovering credentials from local environment...
✨ info si ✓ Found 3 credential(s) in local environment
✨ info si
✨ info si Creating AWS Credential component "aws-credential-dev"...
✨ info si ✓ Component created with ID: 01KC7YBC03EJH2TAM5K4XTX1GE
✨ info si Creating secret data...
✨ info si ✓ Secret created with ID: 01KC7YBEWJAC0K3Q7K1QQ22R17
✨ info si Attaching secret to component...
✨ info si ✓ Secret attached to component
✨ info si
✨ info si ✓ Credential created successfully!
✨ info si Component ID: 01KC7YBC03EJH2TAM5K4XTX1GE
✨ info si Secret ID: 01KC7YBEWJAC0K3Q7K1QQ22R17
✨ info si Secret Name: aws-credential-dev
✨ info si Change Set ID: 01KC7YBATRTKY603YKW5WAZXQ0By using --use-local-profile, the CLI will read the credentials from your environment. You can also pass --interactive and it will prompt the user for the parameters.
INFO
Most things in System Initiative can be done from the Web Application, AI Agent, or the Public API. Creating secrets can only be done through the Web Application and the Public API, as we believe it is fundamentally insecure to feed secrets to an LLM.
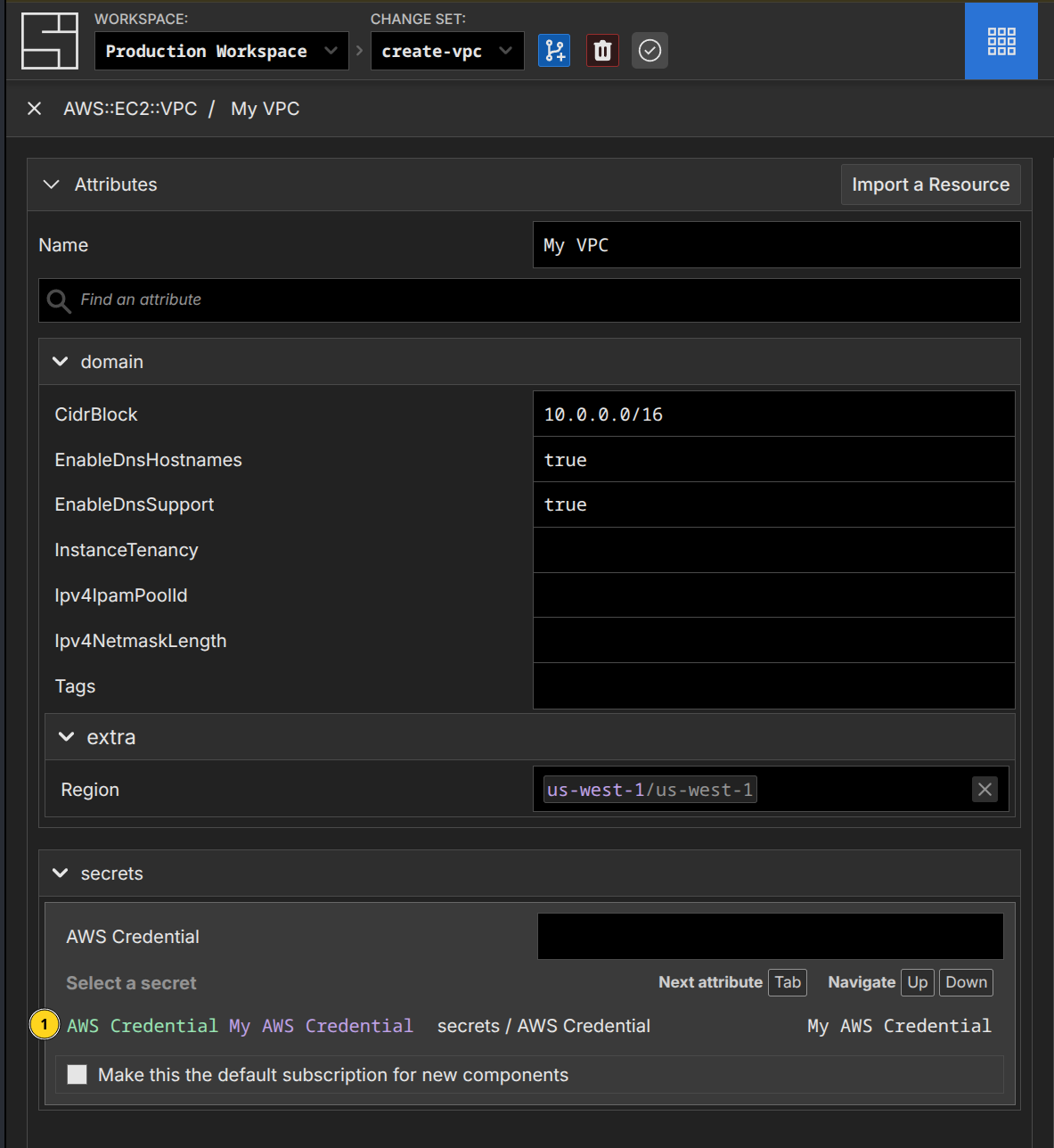
Subscribe to a Secret
To use a secret, you subscribe to the secret value from the component that needs it.
> Create a AWS VPC using the My AWS Credential secret
● VPC created successfully in the "create-vpc" change set with:
- CIDR Block: 10.0.0.0/16
- Region: us-west-1
- Credential: My AWS Credential
You can now apply this change set to create the VPC in AWS, or
make additional changes first.Reference the name of the specific credential you want to subscribe to in the prompt.
Updating a Secret
$ si secret update "aws-credential-dev" --use-local-profile
✨ info si Creating change set: Update secret - 1765498777287
✨ info si Looking for component: aws-credential-dev
✨ info si Found component: aws-credential-dev (01KC7YRCH5XDZ66J848MFY4PKA)
✨ info si Found secretId in component: 01KC7YRD7W8GAMXTC6SZPNTK1B
✨ info si Found secret: aws-credential-dev (01KC7YRD7W8GAMXTC6SZPNTK1B)
✨ info si Discovering credentials from local environment...
✨ info si ✓ Found 3 credential(s) in local environment
✨ info si
✨ info si Updating secret "aws-credential-dev"...
✨ info si ✓ Secret updated: 01KC7YRD7W8GAMXTC6SZPNTK1B
✨ info si
✨ info si ✓ Secret updated successfully!
✨ info si Secret ID: 01KC7YRD7W8GAMXTC6SZPNTK1B
✨ info si Secret Name: aws-credential-dev
✨ info si Change Set ID: 01KC7YTW94K3BKRD91X7PRJ6PNBy using --use-local-profile, the CLI will read the credentials from your environment. You can also pass --interactive and it will prompt the user for the parameters. You can change the name of the secret by passing --name and/or the description by passing --description.
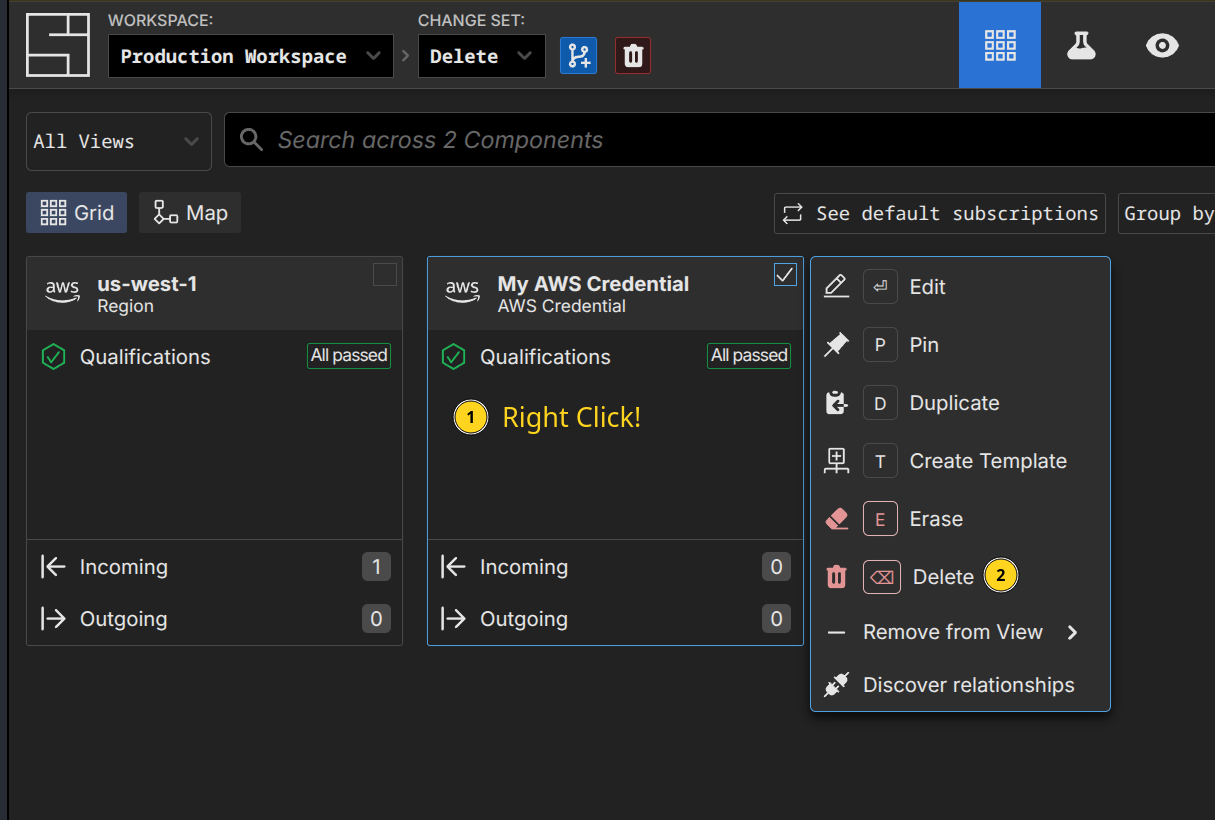
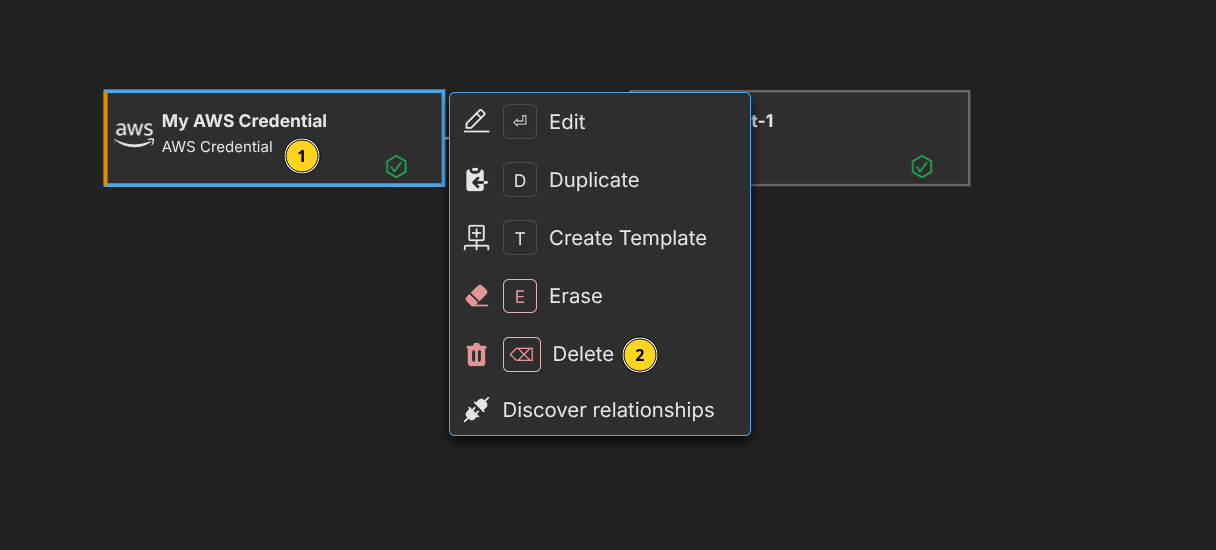
Delete a Secret
You can delete (or erase) secrets like components.
TIP
When a secret is deleted, it cannot be recovered, even from within a change set.
Reference the name of the specific secret you want to delete or erase in the prompt.
> Delete the My AWS Credential secret
● The "My AWS Credential" secret has been deleted